Firewalls as intermediary networking devices have played an important role in protecting a company or organization’s internal servers and hosts, but with networking functionality virtualized (NFV), more and more company applications are moved to the public cloud and the traditional security perimeter now becomes obscure. Before the advent of virtualized firewalls, physical firewalls continued to provide security for public cloud in a similar way to traditional network design. Usually the firewall is placed in the aggregation layer and all traffic from different tenants is routed to physical firewall and the firewall obviously needs multi-tenants support (figure 1 left).
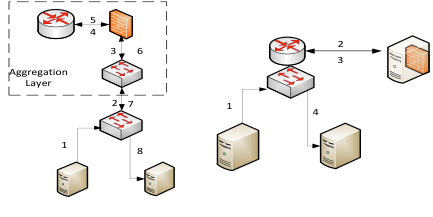
Figure 1. Physical firewall and NVF-like firewall solution in data center
With this solution the traffic between servers in two different security zones will be routed to the aggregation layer router and the firewall enforces the security policy the same way as it used to in enterprise environment. The drawback of this solution is obvious: all traffic even all internal traffic between VMs will be routed to aggregation layer that makes the system less scalable. When the traffic increases to some point that the physical firewall cannot handle, then the physical firewall has to upgraded or a load balance device added for traffic distribution.
An alternative solution to address this issue is to move the physical firewall function to NFV-like deployment, i.e. firewall running in a VM. If VMs hosting different applications need separation, they connect to the firewall NFV and the security policy will be enforced inside the VM. When there is more need, a new firewall NFV can be instantiated along with the application VMs (illustrated as figure 1 right). With NFV each tenant can be thought of as one virtual domain and security can be enforced within each tenant domain, and the traffic within one virtual domain can be optimized e.g. if all VMs are hosted in one rack, the traffic even will not go out of the rack.
When a firewall is deployed as a VM there are some challenges:
– The networking security perimeter shouldn’t change with dynamic VM migration;
– Security information should be carried along the data path within the tenant domain
– The Virtual Appliance may need to migrate to maximize the networking performance
It is non-trivial to implement all those goals with the existing infrastructure because existing configuration-based networking controllers lack the ability to distribute the traffic in a dynamic way. Controller plugins can provide some levels of programmability but the overall networking scalability issue still exists.
IO Visor creates a run-time extensible data plane that allows NFV vendors or customers to define their packet processing logic dynamically. IO visor provides the ability to create a module running in the hypervisor of each data center server and to create a virtual Fabric Overlay on top of it. By overlaying the networking dynamically and logically IO visor can keep the application VMs protected. The firewall can run either in a static networking environment or in a dynamic networking environment with IO visor platform running underneath. Additionally with IO visor’s programmability users can carry and interpret security information in their own way without NFV’s awareness, building up another layer of networking transparency to deploy the virtual security devices like NFV firewall. Finally IO visor can help optimizing the network performance, e.g. In the above example if there is a VM migration in a tenant domain and that lead to sub-optimal networking performance, the user can create its own NFV by describing networking functionality (optimization algorithm) in IO visor framework and load it run-time without waiting for the delivery from NFV vendor or any 3-rd party. This will significantly reduce the NFV delivery time.
In summary IO visor can help security via NFV-based architectures to be deployed in data center transparently and allows for more extensibility with the ability to add security features quickly.
—
About the author of this post
 Jianwen Pi
Jianwen Pi