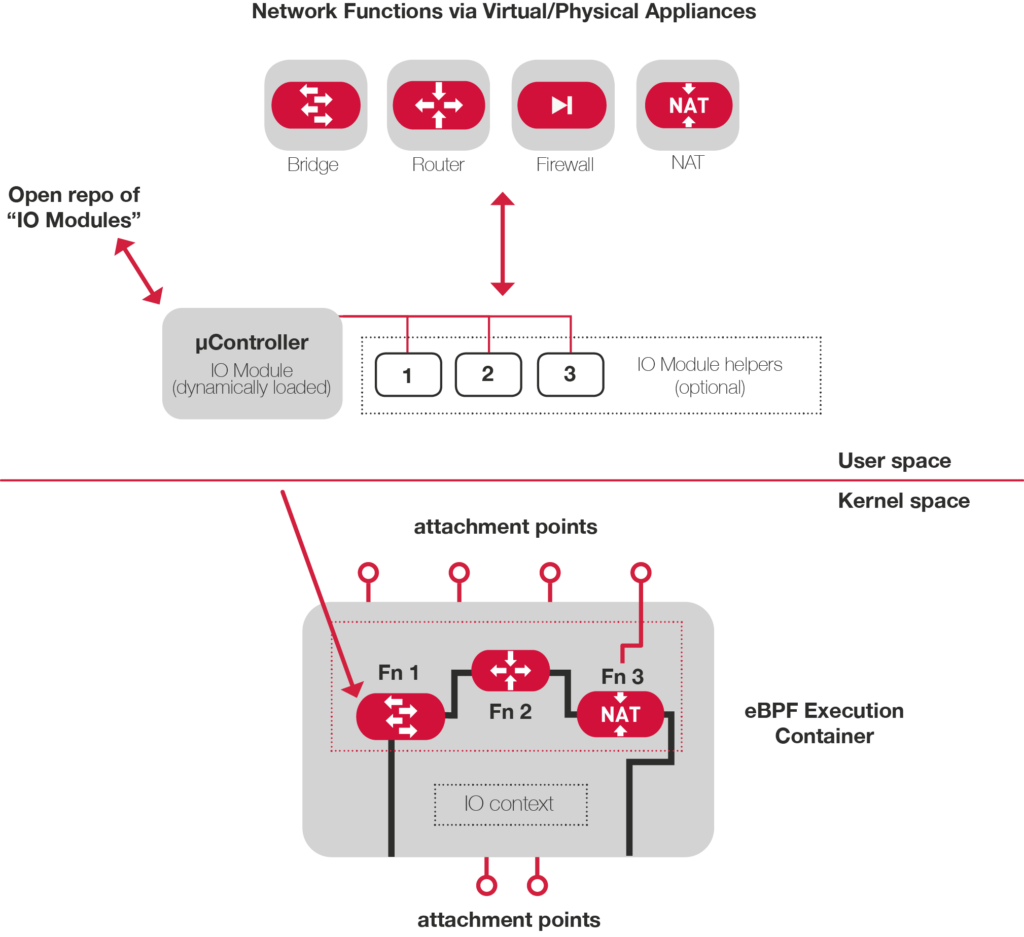
IO Visor has been in use across a variety of use cases. The following are a few examples:
Tracing
BCC or BPF Compiler Collection is a toolkit leveraging eBPF for creating kernel based tracing programs. Functions include kprobes, uprobes, tracepoints, USDT probes and more. Some use cases can be found below:
Brendan Gregg’s blog on using bcc for MySQL tracing:
A presentation by Brenden Blanco and Ali Khayam of PLUMgrid on tracing for OpenStack clouds:
Networking
IO Visor Project enables advanced networking functions (L3, NAT, …) to be implemented in-kernel fully distributed across N compute nodes and chained in-kernel to create any arbitrary “network topology” moving past a virtual/physical appliance type of deployment.
A presentation by William Tu of VMware on using eBPF to offload OVS:
A presentation by F. Risso, M. Bertrone, and M. Bernal on IO Visor and OVN:
A presentation by Yunsong Lu and Yan Chen of Huawei on using IO Visor for Ethernet driver:
A presentation by Yunsong Lu on using eBPF for virtual networking:
Containers
IO Visor is enabling container technologies such as Docker, Mesos, and Kubernetes for virtual networking, security, and policy enforcement. New projects are emerging that are leveraging eBPF and XDP for containers.
Cilium is an experimental project using eBPF and XDP to provide fast in-kernel networking and security policy enforcement for containers. For more information, please visit the Cilium Github.
Presentations by Thomas Graf of Cisco on Cilium:
- Cilium: Networking & Security for Containers with BPF & XDP
- Fast IPv6 Container Networking with BPF and XDP
Mesosphere’s Sargun Dhillion presents the container networking options including eBPF:
A blog by Michael Schubert of Kinvolk on using eBPF from Go, leveraging Weave Scope for Weaveworks:
Security
IO Visor Project enables security functions (micro-segmentation, security groups and firewalls) to be implemented in-kernel and distributed, hence providing the optimal enforcement point for application traffic without the need to hairpin traffic through security appliances. An example of its application to a security problem is seccomp (SECure COMPuting), which implements fencing of applications, by leveraging eBPF as the backend.
A presentation by Brenden Blanco and Deepa Kalani of PLUMgrid on securing microservices:
A video and presentation by Eric Leblond of Stamus Networks on how Suricata could leverage eBPF to mitigate attacks:
Monitoring
IO Visor Project enables a broad spectrum of real-time performance and monitoring applications to be built directly inside the kernel.
Real-time VXLAN tunnel monitoring chord graph:
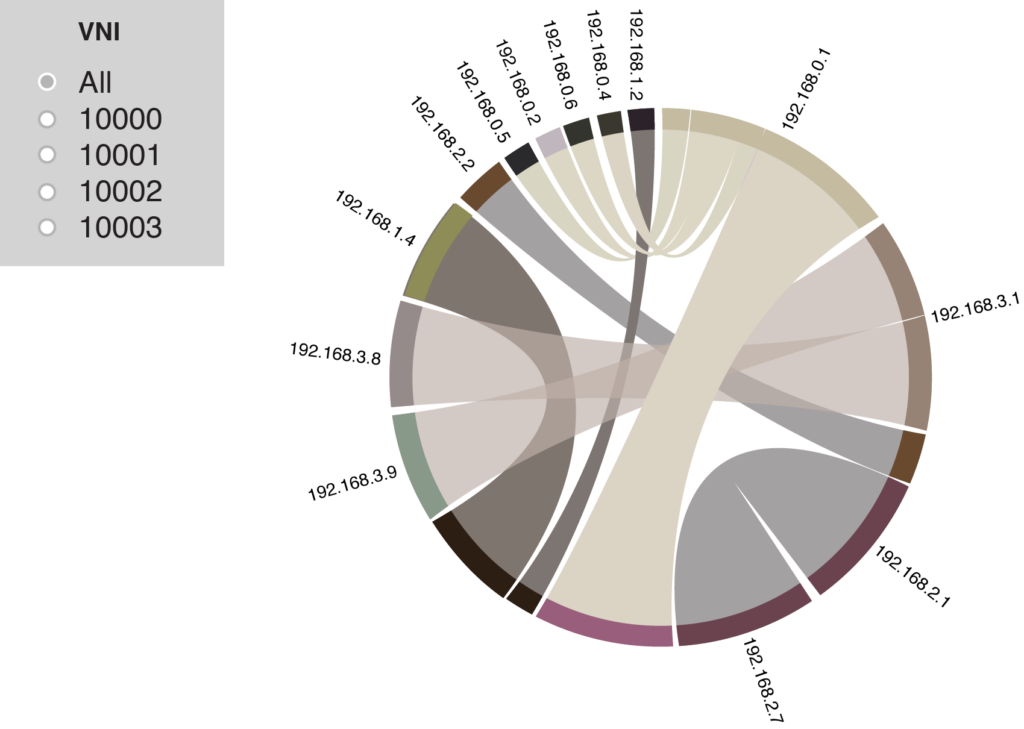
Monitoring mobile application performance by Wang Nan of Huawei:
Hardware Offload
A presentation by Netronome’s Dinan Gunawardena and Jakub Kicinski:
A video and presentation byJakub Kicinski and Nic Viljoen of Netronome: